Grandstream Phone Vulnerability Security Issue Remote Backdoor Connection to 207.246.119.209:3478
Have you checked your router/firewall logs and disconcertingly see connections to an unknown IP 207.246.119.209:3478 from your Grandstream VOIP phones?
![]()
You're not alone and the Grandstream forums have discussed this issue.
However, even their own staff do not seem to be aware or are not disclosing what this connection is.
It is Grandstream's GDMS.cloud UCM Remote connect feature
This is the establishment to the STUN server and you can find their list of servers/info here.
It allows you to remotely provision and manage your devices and is enabled by default at least on later/newer firmware versions. While this is a great feature and helpful for provisioning, it is still concerning since there is no obvious warning or disclosure on this when purchasing the phone. It represents a huge tradeoff of security/privacy vs convenience.
The concern is that Grandstream, the government and hackers could potentially compromise your phone, your calls and even your network is it is essentially a back door to your network despite being on a protected LAN and firewall. Others share the same concern here: https://www.voip-info.org/forum/threads/grandstream-backdoor.24096/
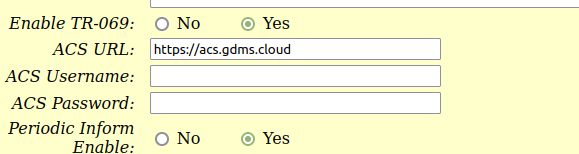
How To Disable The Remote 3478 Connection
Under "Advanced Settings" -> Enable TR-069 disable it by setting to to "No" and then click "Apply".
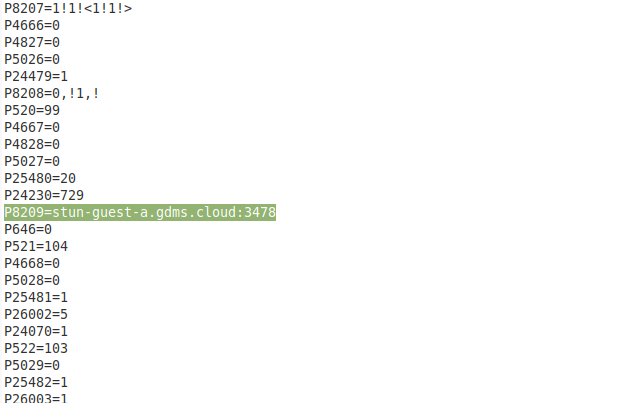
Manual Edit Cannot Disable
You can remove the P8209 entry or make it null or change it, and upload the config file, but the firmware seems to just default back and re-enable the STUN server. The only solution is to block any DNS lookups to that host and block all traffic to that UDP port.
Tags:
grandstream, vulnerability, backdoor, router, firewall, logs, disconcertingly, connections, ip, voip, forums, disclosing, gdms, ucm, feature, establishment, stun, server, servers, info, allows, remotely, provision, devices, enabled, default, newer, firmware, versions, concerning, disclosure, purchasing, disabled, admin, config, entry, null, upload, enable, dns, lookups, udp,
