Wazuh / OSSEC Install and Configuration Howto Tutorial Guide for Monitoring Agents SIEM
How To Install Wazuh Server / Quickest Installation
Wazuh (forked from the well known OSSEC project) is a full SIEM (Security Information Event Management) that works extremely well with the platforms it natively supports as an "Agent", which allows you to do scans of everything such as all processes running, CVE vulnerability check, incident reporting etc...
Prerequisites:
A lot of issues with Wazuh seem to be caused by issues relating to a non-clean system. This means that you should have a minimal install of Linux (eg. no GUI, nothing but Base + SSH) before installing. Some issues that occur when you have the GUI and extra packages may be that the install fails to complete and hangs on Kibana, or that Kibana won't start.
You can solve that problem with set_cap but I normally find the install is still broken beyond repair, so make sure you have a fresh, minimal OS before installing.
This is the easiest way to handle the installation Wazuh:
Recommended tools before:
apt install gnupg sudo wget
The unattended install makes things a breeze to configure all of the components automatically including Kibana, Elasticsearch, Filebeat and the Wazuh-Manager itself. This is the easiest way to do the installation, and arguably the official documentation for the Step-By-Step installation from Wazuh is missing some key steps/components.
wget https://packages.wazuh.com/resources/4.2/open-distro/unattended-installation/unattended-installation.sh
bash unattended-installation.sh
After Successful Installation How Do I Login To Wazuh?
You should see output like below, the last line contains the Kibana/Wazuh login details and you then access it at the IP of the VM/container/server that Wazuh was installed to:
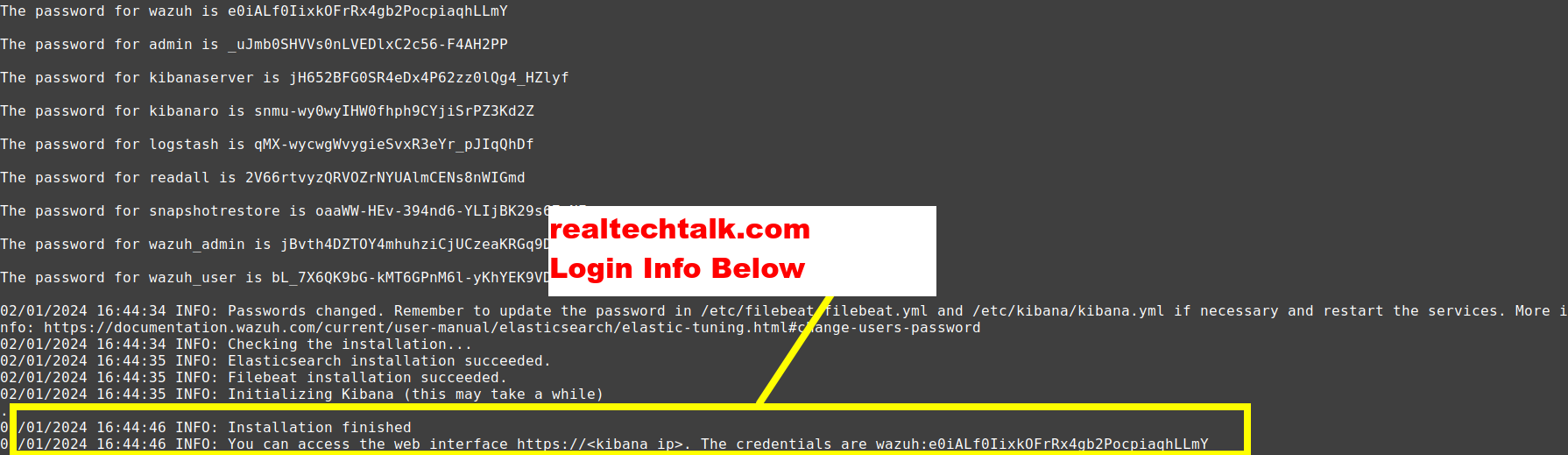
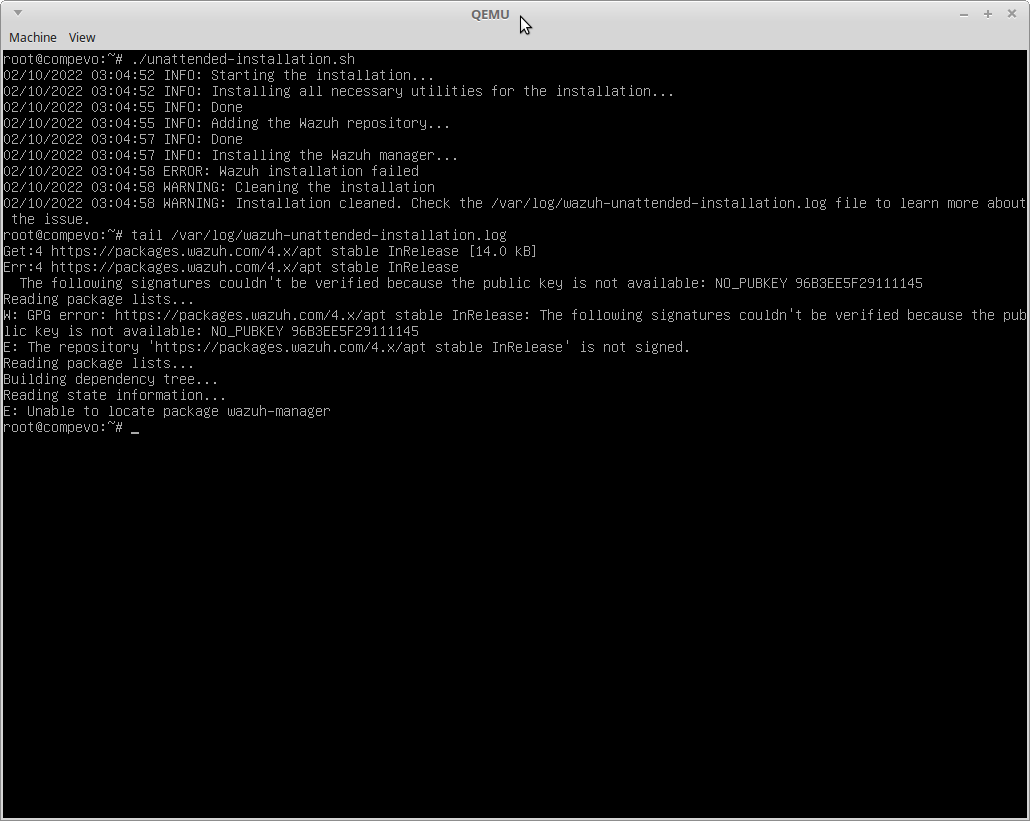
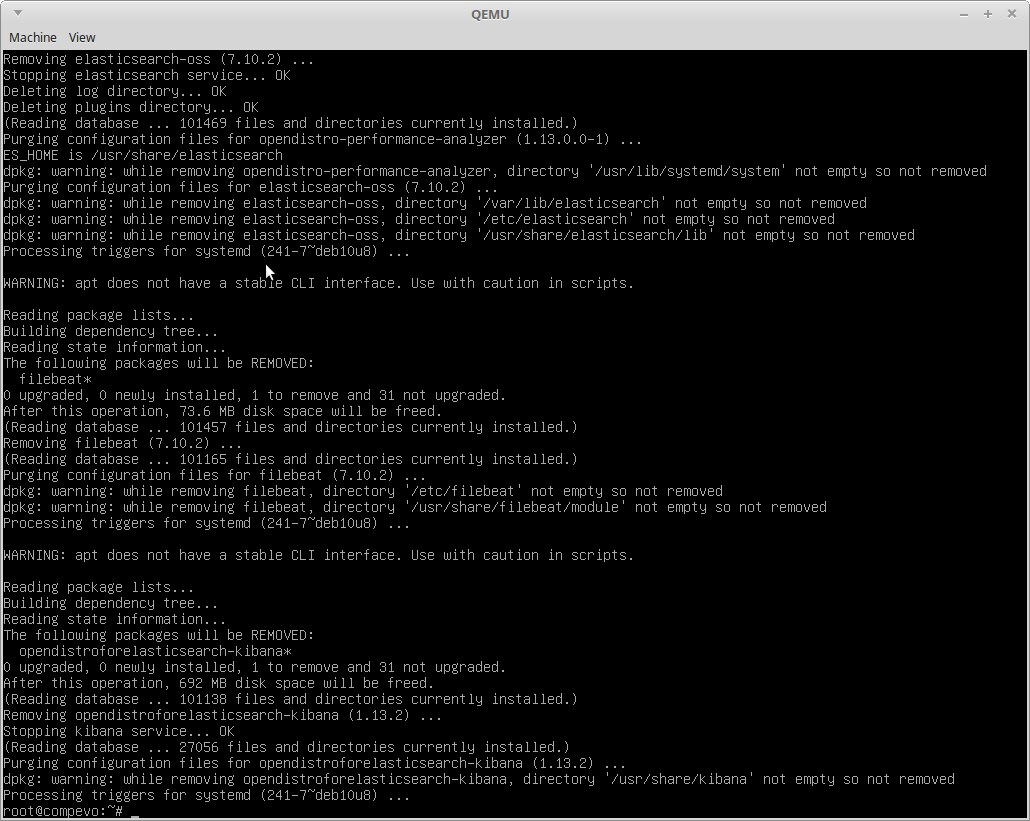
"The following signatures couldn't be verified because the public key is not available".
The error is a red herring because the install script does attempt to add the key using apt-key, but it will fail if you don't have gnupg installed.
Install gnupg to solve the public key error in the install script and run it again
Error: Wazuh Kibana Plugin Could Not Be Installed
This is odd, but you need sudo installed, even if running as root or the install will fail.
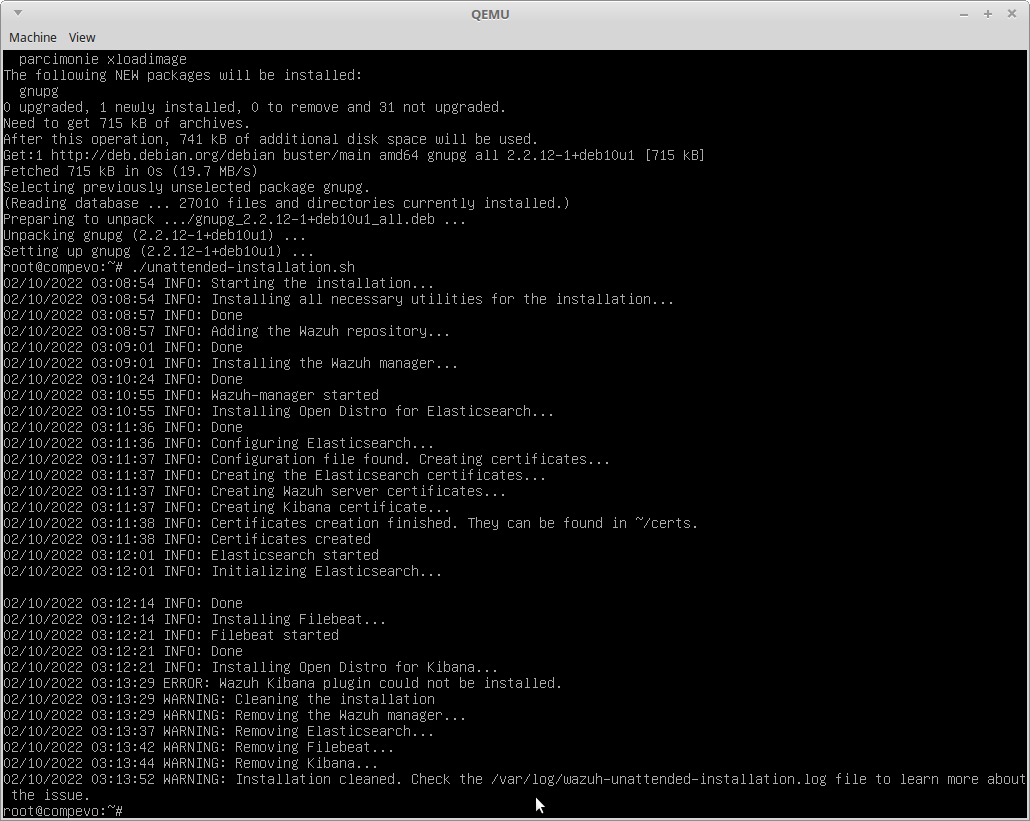
Check the log:
How To Install Wazuh Agent To Debian/Mint/Ubuntu apt Linux Servers
Install the GPG Key and the repo
curl -s https://packages.wazuh.com/key/GPG-KEY-WAZUH | apt-key add -
echo "deb https://packages.wazuh.com/4.x/apt/ stable main" | tee -a /etc/apt/sources.list.d/wazuh.list
apt update
Install Wazuh with the Specified Manager IP
WAZUH_MANAGER="10.10.10.11" apt-get install wazuh-agent
Enable and Start the Wazuh Agent
systemctl enable wazuh-agent
systemctl start wazuh-agent
#** Change the IP above 10.10.10.11 to the IP of your Wazuh Server IP
Need to change the IP of your Wazuh manager?
Edit /var/ossec/etc/ossec.conf
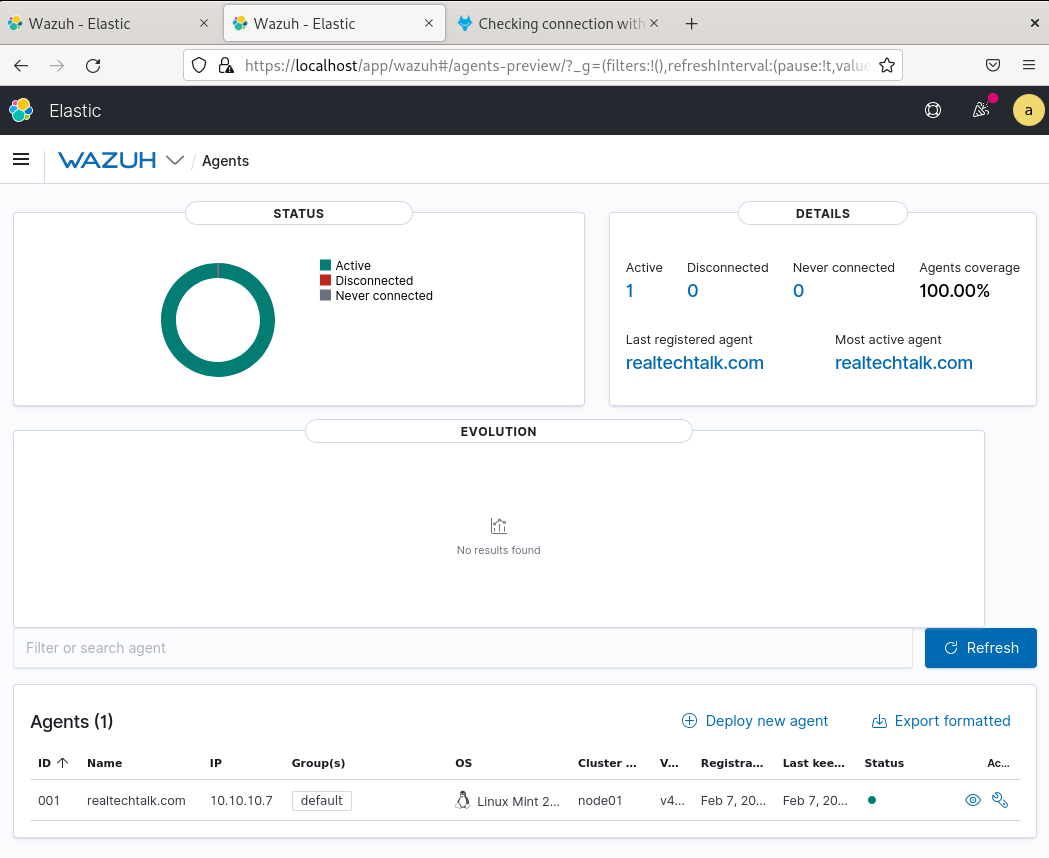
Can't see your Agent registered?
Check the log file:
cat /var/ossec/logs/ossec.log
Check the Wazuh troubleshooting document.
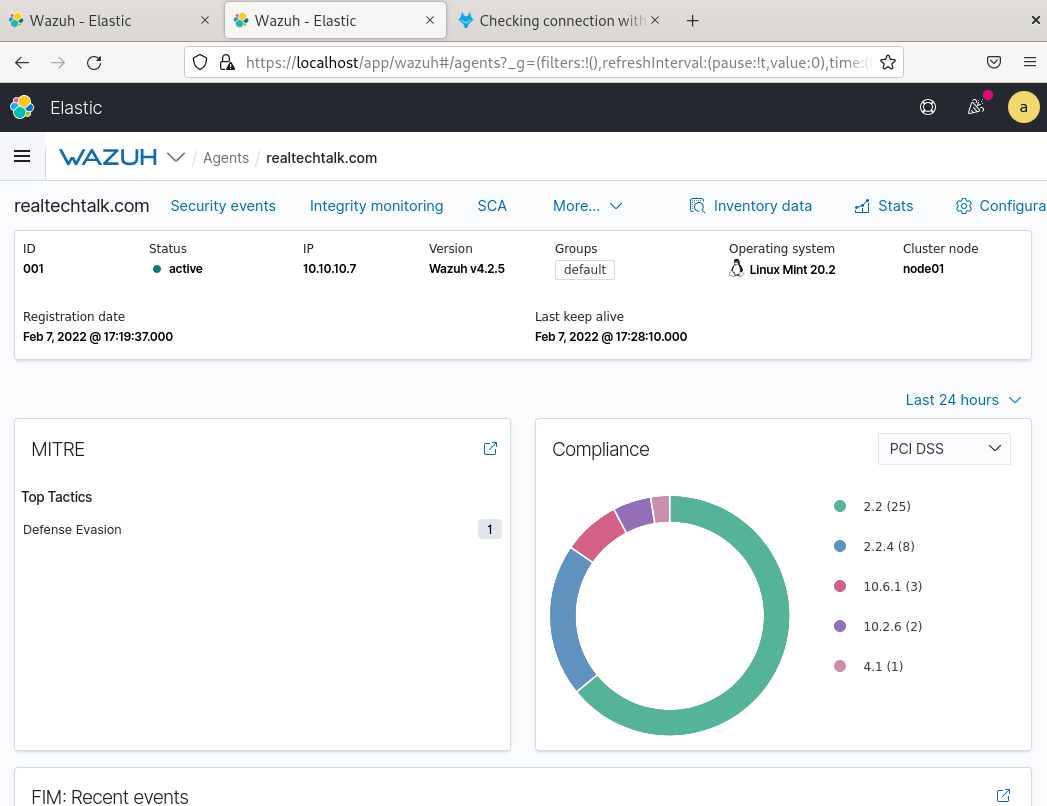
View the Agent On The Manager:
How To Add Agentless Monitoring via SSH for other devices like routers/firewalls/OS's
Agentless means that nothing is installed on the device/server that we monitor, it is all done using the agentless service from the Wazuh Manager which runs as the user "ossec"
- Note that agentless is mainly relegated to detecting config changes on specific directories etc.. and agentless devices DO NOT show up under the list of "Agents" inside Wazuh GUI. Instead you have to check the log and can possibly create your own custom dashboard and visualization to track these types of devices.
- Note that this all occurs on the Wazuh Manager.
- Note that the user that does the monitoring is "ossec" so that user must be able to authenticate to the agentless side
Make sure you have the expect instead on the wazuh-manager or agentless monitoring will fail (especially if you are using password auth)
apt install expect
1.) Use /var/ossec/agentless/register_host.sh
The format of this script is that we can just use this format and do pub key auth:
/var/ossec/agentless/register_host.sh add user@host
You can also specify a password to login with
/var/ossec/agentless/register_host.sh add user@host thepassword
For devices like Cisco you can specify an additional password which is the enable password
/var/ossec/agentless/register_host.sh add user@host thepassword ciscoenablepassword
You can pass the parameter list to show the list of agentless devices:
./register_host.sh list
*Available hosts:
realtechtalkcom@10.10.10.11
realtechtalkcom@10.10.10.7
If you are using pub key authentication run this:
sudo -u ossec ssh-keygen
Then copy the ossec /var/ossec/.ssh/id_rsa.pub contents to .ssh/authorized_keys on the remote host
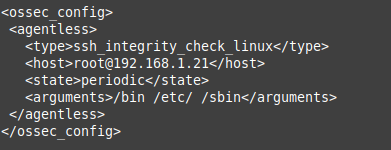
2.) Edit ossec.conf and add the agentless rule you want
vi /var/ossec/etc/ossec.conf
Modify this part to match what you need, for example I took the output above of "realtechtalkcom@10.10.10.7" and added it to the "host" section in the XML below.
Note that the agentless XML below will be inside of an ossec_config
Example of being inside ossec_config
3.) Restart wazuh-manager
systemctl restart wazuh-manager
4.) Observe it
It should be good, if you get an error like below it is because you need to install "expect" on the manager.
cat /var/ossec/logs/ossec.log
2022/02/11 17:55:06 wazuh-agentlessd: INFO: ssh_integrity_check_linux: realtechtalkcom@10.10.10.7: Started.
2022/02/11 17:49:17 sca: INFO: Starting evaluation of policy: '/var/ossec/ruleset/sca/cis_debian10.yml'
2022/02/11 17:49:17 wazuh-modulesd:syscollector: INFO: Evaluation finished.
2022/02/11 17:49:18 wazuh-syscheckd: INFO: (6009): File integrity monitoring scan ended.
2022/02/11 17:49:20 wazuh-agentlessd: ERROR: Expect command not found (or bad arguments) for 'ssh_integrity_check_linux'.
2022/02/11 17:49:20 wazuh-agentlessd: ERROR: Test failed for 'ssh_integrity_check_linux' (127). Ignoring.
2022/02/11 17:49:23 sca: INFO: Evaluation finished for policy '/var/ossec/ruleset/sca/cis_debian10.yml'
2022/02/11 17:49:23 sca: INFO: Security Configuration Assessment scan finished. Duration: 6 seconds.
Removing Agentless Hosts
This can only be done by removing all hosts from /var/ossec/agentless/.passlist
There is no way to remove an individual host. For production use you should keep a separate CSV with al ist of IPs and passwords that runs the register_host.sh script for each one.
More documentation on Agentless Monitoring:
https://documentation.wazuh.com/current/user-manual/capabilities/agentless-monitoring/index.html
Troubleshooting
Can't See Agent After Adding It:
Check logs on the agent side, make sure neither side is being blocked by a firewall or other connectivity issue.
cat /var/ossec/logs/ossec.log
2022/02/11 13:35:38 wazuh-agentd: ERROR: (1216): Unable to connect to '10.10.10.11:1514/tcp': 'Connection refused'.
2022/02/11 13:35:44 wazuh-logcollector: WARNING: Target 'agent' message queue is full (1024). Log lines may be lost.
2022/02/11 13:35:50 wazuh-agentd: INFO: Trying to connect to server (10.10.10.11:1514/tcp).
2022/02/11 13:35:50 wazuh-agentd: INFO: (4102): Connected to the server (10.10.10.11:1514/tcp).
2022/02/11 13:35:54 sca: INFO: Evaluation finished for policy '/var/ossec/ruleset/sca/sca_unix_audit.yml'
2022/02/11 13:35:54 sca: INFO: Security Configuration Assessment scan finished. Duration: 35 seconds.
2022/02/11 13:35:54 wazuh-syscheckd: INFO: Agent is now online. Process unlocked, continuing...
2022/02/11 13:35:54 rootcheck: INFO: Starting rootcheck scan.
2022/02/11 13:36:01 wazuh-syscheckd: INFO: (6009): File integrity monitoring scan ended.
2022/02/11 13:37:32 rootcheck: INFO: Ending rootcheck scan.
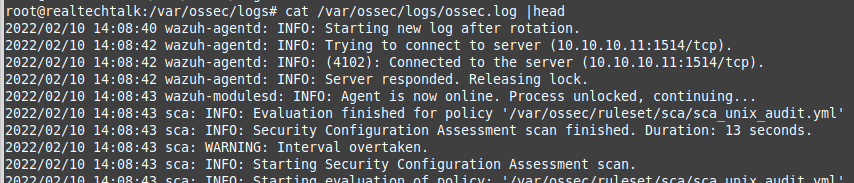
Make sure wazuh-manager is started.
How To Add User To Wazuh
1. Click on the 3 bars on the top left and then click "Security"
2. Click "Internal users" on the left and then "Create internal user"
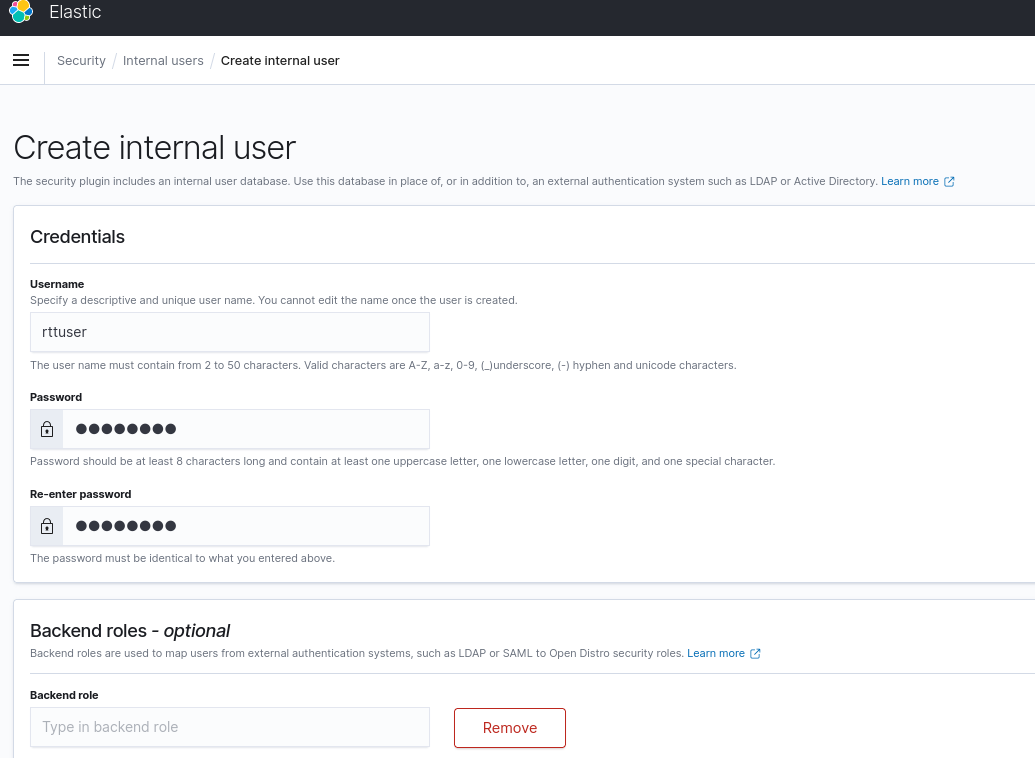
3. Enter Details of The Internal user
*Don't forget to add a backend role like "admin" or you will not be able to do anything in Wazuh.
4. Scroll to the Bottom right and click "Create"
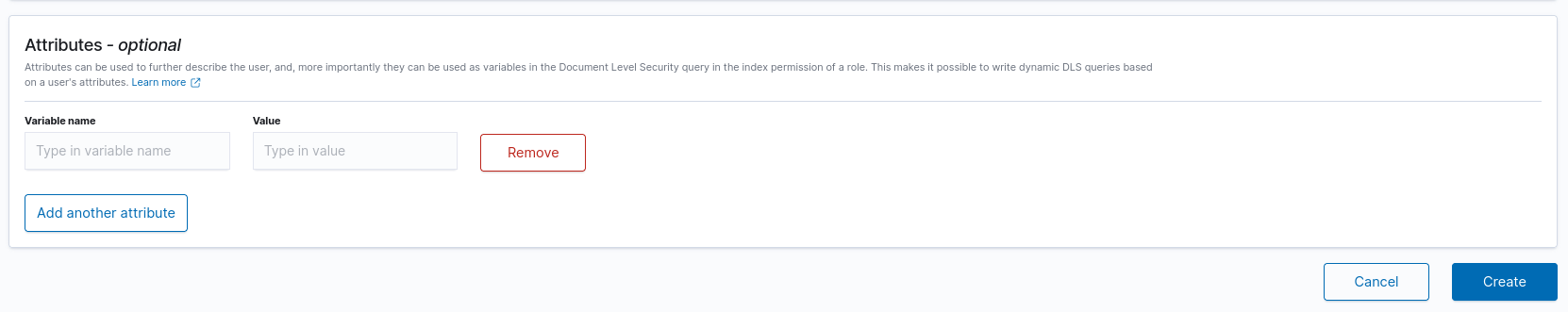
More on Wazuh User Creation and Roles
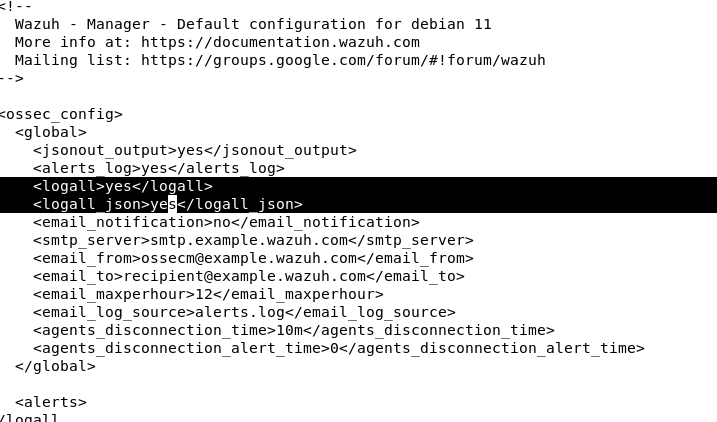
How to Enable Wazuh E-mail Notifications + Logging of ALL events + JSON
Edit /var/ossec/etc/ossec.conf
1. Edit the parameters logall to yes
2. Edit the e-mail_ parameters to what makes sense for you
3. Restart wazuh server with: systemctl restart wazuh-manager
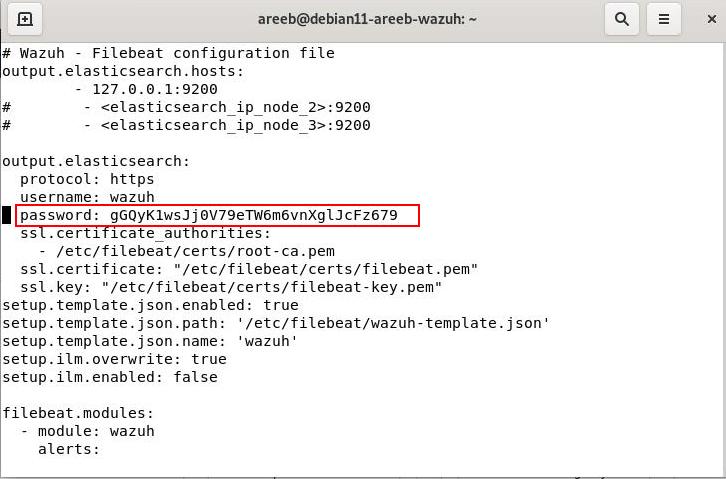
How To Reset/Change The Wazuh Admin Password
You can find the wazuh user password in /etc/filebeat/filebeat.yml and recover or reset it as shown in the password variable "password:" in the screenshot below.
sudo vi /etc/filebeat/filebeat.yml
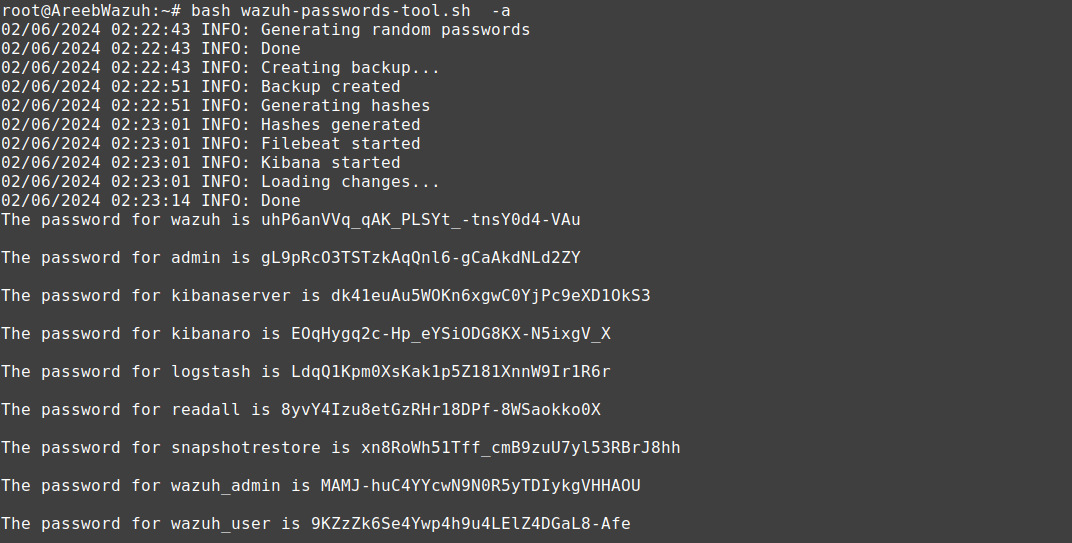
You can run this script as well to change ALL passwords in Wazuh for all users and services:
You can download it from here (change the version to match yours):
https://packages.wazuh.com/4.x/wazuh-passwords-tool.sh
bash wazuh-passwords-tool.sh -a
https://documentation.wazuh.com/4.0/user-manual/elasticsearch/elastic_tuning.html
References:
https://documentation.wazuh.com/current/installation-guide/open-distro/index.html
https://documentation.wazuh.com/current/installation-guide/wazuh-agent/index.html
Tags:
wazuh, install, configuration, howto, tutorial, monitoring, agentshow, server, easiest, unattended, breeze, configure, components, automatically, kibana, elasticsearch, filebeat, wget, https, packages, distro, installation, sh, bash, apt, gnupg, installed, quot, signatures, couldn, verified, herring, plugin, sudo, documentation, deployment, html, debian, mint, ubuntu, linux, servers, gpg, repo, curl, echo, deb, tee, etc, sources, update, specified, ip, wazuh_manager, enable, systemctl, user, users, backend, admin, scroll, creation, roles, notifications, logging, json, edit, var, ossec, conf, parameters, logall, mail_, restart, references, index,
